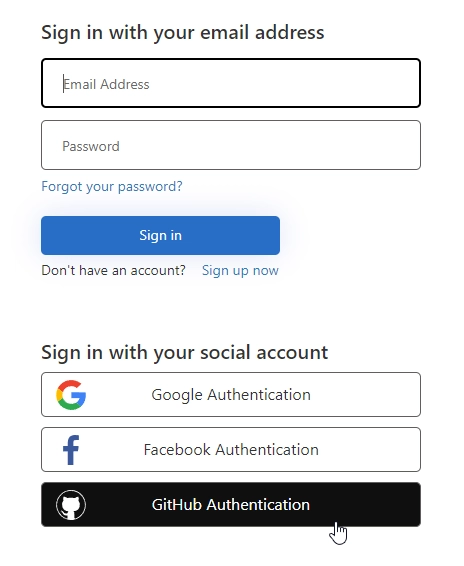
Add GitHub Authentication to Azure AD B2C in public web forms
Follow this instruction for GitHub Identity Provider — you’ll first need to create an OAuth application in GitHub Developer portal:
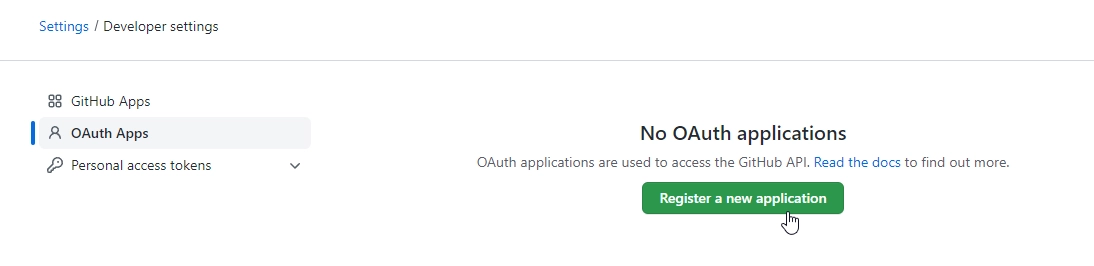
Enter a Name for your application and your homepage URL.
For the Authorization callback URL, enter https://your-tenant-name.b2clogin.com/your-tenant-name.onmicrosoft.com/oauth2/authresp. If you use a custom domain, enter https://your-domain-name/your-tenant-name.onmicrosoft.com/oauth2/authresp. Replace your-domain-name with your custom domain, and your-tenant-name with the name of your tenant. Use all lowercase letters when entering your tenant name even if the tenant is defined with uppercase letters in Azure AD B2C.
Click Register application.
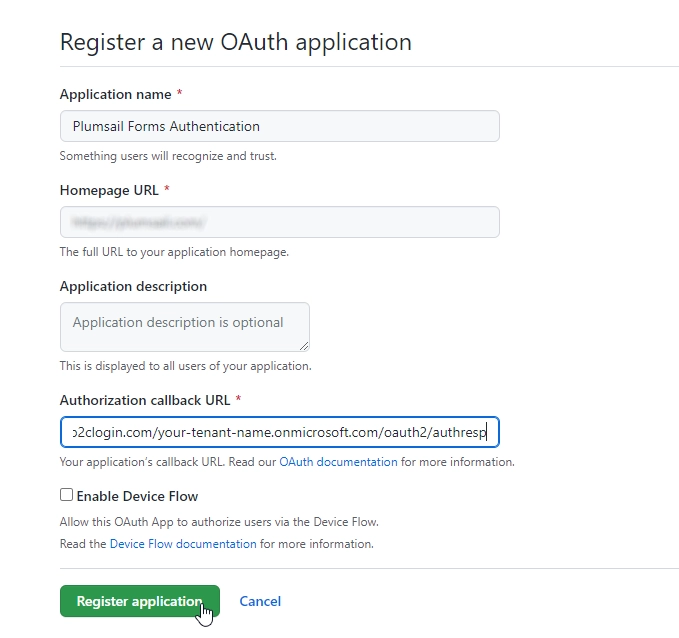
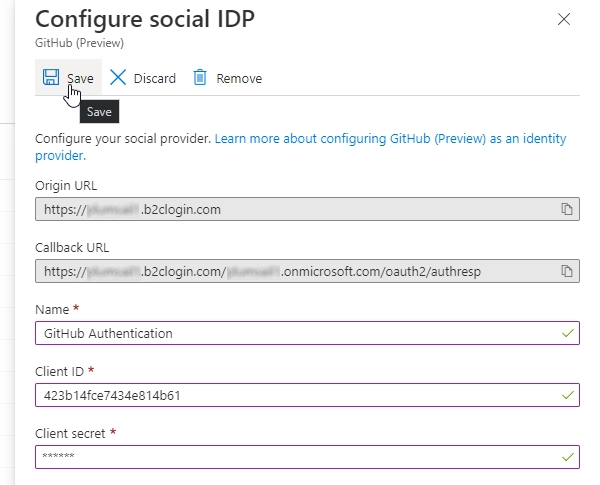
Copy the values of Client ID and Client Secret:
Paste them to GitHub Identity provider in Azure AD B2C:
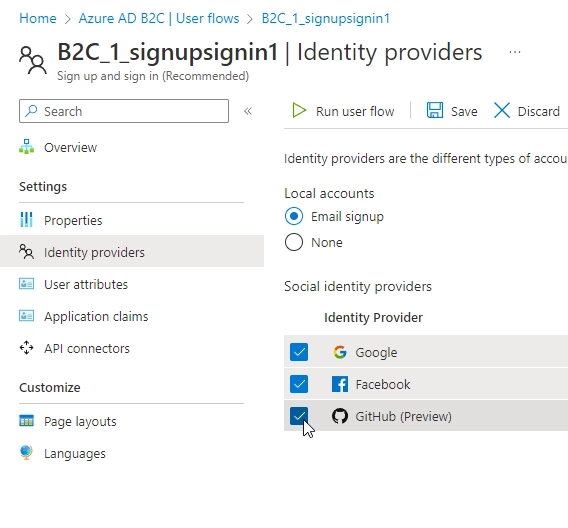
After setting it up, you can add it as an Identity provider to the sign up and sign in flow that you’ve created:
Then, your form users will be able to select GitHub as sign in platform: